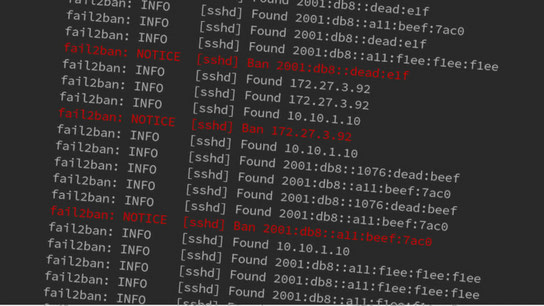
The reaction to this headline from sysadmins who deploy Fail2Ban on an IPv6 enabled system is probably: “Fail2Ban doesn’t support IPv6‽” At least, that seems to be the reaction most admins have posted on forums and social media when they learn that Fail2Ban doesn’t support IPv6. Now Fail2Ban’s IPv4-only limitation is about to be lifted.
Fail2Ban is a tool that identifies unwanted behaviors by monitoring service logs, and can act upon that by banning offending IP addresses temporarily. Until recently, Fail2Ban only supported IPv4 although it’s almost certainly running on many IPv6 capable systems as well.
Update (): Fail2Ban 0.10 with IPv6 support has finally been released. Be sure you upgrade and test your filters and block actions!
Update (): It has been a full year and we’re still waiting for the next release of Fail2Ban. To protect your servers, please consider using an alternative like SSHGuard instead.
For a server running with a standard IPv4/IPv6 dual-stack domain setup, it wouldn’t help much to only block attacks coming in over IPv4. Even after successfully blocking an ongoing brute-force login attack over IPv4, the domain resolution server would return the server’s IPv6 address and the attack could start up again on the newer protocol version without restrictions. Without support for also blocking IPv6 addresses, Fail2Ban wouldn’t accomplish much more than to push more traffic from IPv4 to IPv6. Admittedly, this is an admirable goal in itself, but it’s probably not the effect the system administrator was going for.
Plans to add IPv6 support have been lurking around in the Fail2Ban bug tracker for some years already, with the first known issue [in the current tracker] dating back to 2012. Yet, no fruitful implementation work has happened until this April.
A 800-line pull request from first-time contributor to the Fail2Ban project, Alexander Köppe, prompted regular contributor Serg Brester to finalize and complete the work for Fail2Ban version 0.10. Fail2Ban’s 0.10 branch now contains Mr Köppe’s initial work on IPv6 and Mr. Brester’s continued implementation work. There are also plenty of bug fixes and performance improvements in the 0.10 branch.
Sysadmins responsible for IPv6 enabled systems that deploy Fail2Ban should keep an eye out for the next Fail2Ban release and act fast to update when it becomes available. Fail2Ban doesn’t release on a fixed schedule but releases happen roughly two times per year. If this is any indication, we’ll see the next release sometime towards the end of this summer.
The 0.10 branch is still experimental, but now is a good time to throw your various log files at it and help report issues. It’s still early but if you’re not too faint of heart, you could also start testing the branch and gain some level of IPv6 protection in the process.